Understanding how to navigate the Tor network safely and effectively requires technical knowledge and awareness of its legitimate applications. This guide explains onion search mechanics, practical use cases, and essential safety considerations for researchers, journalists, and privacy-conscious users.
What Exactly Is Onion Search?
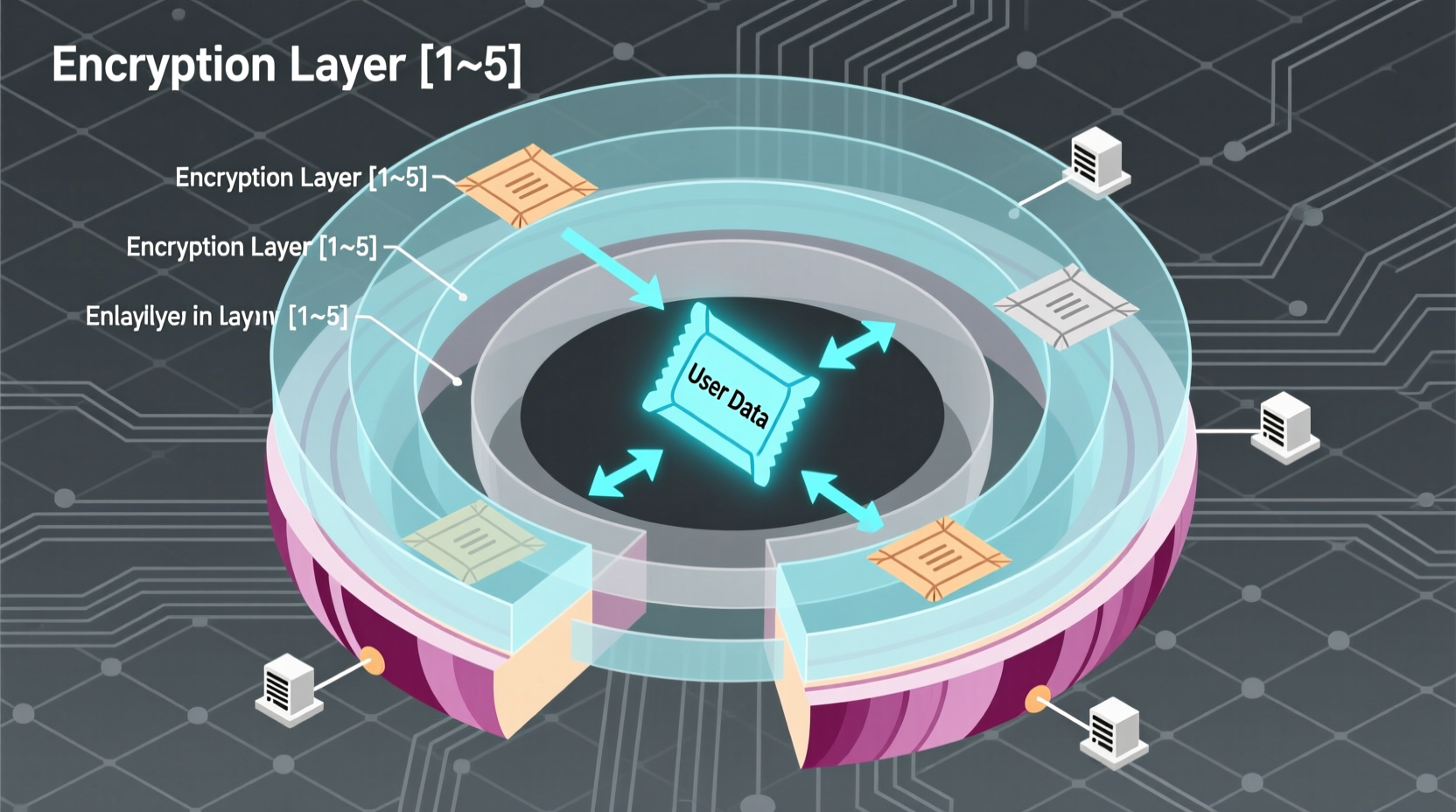
Onion search specifically targets content hosted on the Tor network's hidden services, identifiable by their .onion domain suffix. These addresses represent websites that exist exclusively within the Tor ecosystem, inaccessible through conventional browsers. The "onion" metaphor describes the layered encryption protocol that routes traffic through multiple volunteer-operated servers, each decrypting only enough information to forward the data to the next node.
When you perform an onion search, you're not querying the standard internet but rather the decentralized Tor network. This requires:
- The Tor Browser installed and properly configured
- Specific onion search engines like Ahmia or Not Evil
- Understanding that results differ significantly from conventional search engines
Technical Mechanics Behind Onion Routing
Onion routing works through a sophisticated multi-layer encryption process. When initiating a connection to an onion service:
- Your Tor client builds a circuit through three randomly selected relays
- Each layer of encryption gets peeled off at successive relays (like an onion)
- The final relay (exit node) delivers your request to the destination server
- Return traffic follows the same path in reverse with re-encryption at each step
This architecture ensures no single relay knows both the origin and destination of traffic. The Tor Project, which maintains this technology, emphasizes that onion services provide end-to-end encryption between client and server, unlike standard Tor browsing which terminates encryption at the exit node.
Legitimate Applications of Onion Search
Despite common misconceptions, onion search serves numerous legitimate purposes:
- Whistleblower protection: News organizations like The New York Times and The Guardian operate onion services for secure document submission
- Privacy preservation: Users in countries with internet surveillance access censored information
- Secure communications: Activists in restrictive regimes organize without exposure
- Research purposes: Academics study network security and censorship circumvention techniques
The Electronic Frontier Foundation (EFF) documents numerous cases where onion services have protected human rights activists. Their 2023 report highlights how Iranian protesters used Tor to coordinate demonstrations while avoiding government tracking (eff.org/deeplinks/2023/09/tor-iran-protests).
Onion Search vs. Conventional Web Search: Key Differences
| Feature | Onion Search | Conventional Search |
|---|---|---|
| Access Method | Requires Tor Browser | Standard browsers |
| Content Indexing | Limited, specialized engines | Comprehensive commercial indexes |
| Speed | Slower (multiple encryption layers) | Faster direct connections |
| Privacy Level | High (conceals both parties) | Low (visible to ISPs, trackers) |
| Content Verification | Challenging (no central authority) | Established verification systems |
Evolution of Onion Routing Technology
The development of onion routing has followed this progression:
- 1995-1998: Initial concept developed by US Naval Research Laboratory researchers Paul Syverson, Michael Reed, and David Goldschlag
- 2002: First public implementation (Tor prototype) released
- 2004: Tor project launched as open-source software
- 2010: Introduction of v2 onion services with improved security
- 2021: Deployment of v3 onion services featuring stronger cryptography
- 2023: Over 200,000 onion services active according to Tor metrics (metrics.torproject.org)
Critical Safety Considerations
While onion search offers privacy benefits, users must understand these limitations:
- Not absolute anonymity: Advanced adversaries may deanonymize users through traffic analysis
- Malware risks: Hidden services may host malicious content without standard security protections
- Legal boundaries: Accessing certain content may violate laws in your jurisdiction
- Performance trade-offs: Encryption layers significantly reduce connection speeds
The National Institute of Standards and Technology (NIST) warns that "while Tor provides strong anonymity guarantees, it cannot protect against all forms of traffic analysis or endpoint compromise" (csrc.nist.gov/publications/detail/sp/800-113/rev-1/final). Security experts recommend using Tor in conjunction with a reputable VPN for enhanced protection when accessing onion services.
Practical Guidance for Responsible Usage
If you require onion search capabilities for legitimate purposes:
- Download Tor Browser only from the official Tor Project website
- Never disable JavaScript filtering in Tor Browser's security settings
- Use bridges if Tor access is blocked in your region
- Avoid downloading files from untrusted onion services
- Maintain separate browsing profiles for different activities
Researchers at Carnegie Mellon University's cybersecurity program emphasize that "proper configuration and disciplined usage patterns determine the effectiveness of onion routing more than the technology itself" (cylab.cmu.edu/research/techreports/2022/tr_cylab22001.html).
Conclusion: Balancing Privacy and Security
Onion search represents a powerful tool for privacy-conscious internet users when applied responsibly. Its technical architecture provides meaningful protection against surveillance while enabling access to information in restrictive environments. Understanding both its capabilities and limitations helps users make informed decisions about when and how to incorporate onion search into their digital security practices. As with any technology, responsible usage requires ongoing education about evolving threats and best practices.











 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4