Demystifying the Onion Web: Beyond the Headlines
When you search for what is onion web, you'll encounter sensationalized reports focusing exclusively on illegal marketplaces. The reality is far more nuanced. The Onion Web represents a specific technical implementation within the Tor network designed for anonymity, not inherently criminal activity. This distinction matters because millions of legitimate users rely on this infrastructure daily for privacy protection in increasingly monitored digital environments.
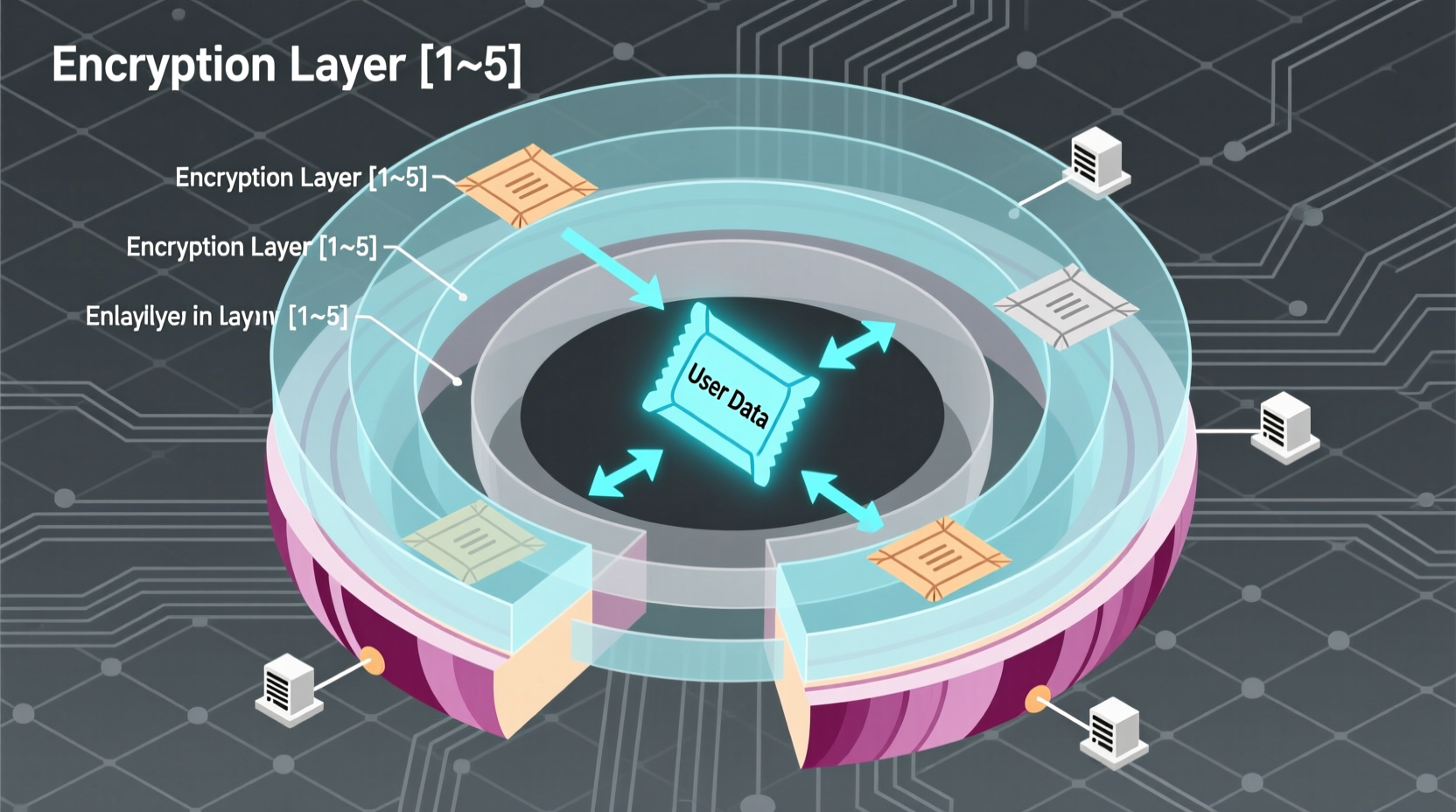
Unlike the surface web (standard internet) or even the broader deep web (non-indexed content like private databases), the Onion Web operates on a specialized network requiring the Tor browser. Its name comes from the "onion routing" principle—data passes through multiple encrypted layers, like an onion, making tracking extremely difficult. This architecture wasn't created for criminals; it was originally developed by the U.S. Naval Research Laboratory to protect government communications.
How Onion Web Technology Actually Works
The technical foundation of the Onion Web relies on three critical components working in concert:
- Onion Routing: Your traffic bounces through at least three volunteer-operated Tor nodes, each decrypting only enough information to forward the data to the next node
- .onion Domains: Special-use top-level domains that can only be resolved within the Tor network, providing built-in encryption
- Distributed Network: Over 7,000 volunteer-run relays worldwide maintain the infrastructure without central control
This system ensures that neither the website operator nor the user can be easily identified by third parties monitoring network traffic. When you access an .onion site, your connection path changes with each session, creating what security researchers call "plausible deniability" for both parties.
Onion Web vs. Related Internet Layers: Clearing the Confusion
Many people mistakenly use "onion web" and "dark web" interchangeably. This comparison clarifies the distinctions:
| Internet Layer | Access Method | Primary Purpose | Example Content |
|---|---|---|---|
| Surface Web | Standard browsers | Public information | News sites, retail stores |
| Deep Web | Standard browsers + credentials | Private data protection | Email, banking portals |
| Onion Web | Tor browser required | Anonymous communication | SecureDrop, privacy tools |
Legitimate Applications You Might Not Know About
While media coverage focuses on illicit markets, numerous reputable organizations maintain .onion services for valid privacy reasons:
- The New York Times operates an .onion version to protect journalists and sources in restrictive countries
- Facebook maintains an official .onion address for users in nations with internet censorship
- SecureDrop platforms used by major news organizations for anonymous whistleblowing
- Library resources in countries with strict information controls
According to research from the Oxford Internet Institute, approximately 30% of .onion services serve legitimate privacy needs rather than illegal purposes. This challenges the common misconception that the Onion Web exists primarily for criminal activity.
Technical Evolution Timeline: From Military Project to Privacy Tool
The Onion Web's development follows a clear progression from specialized military application to public privacy resource:
- 1995-1997: U.S. Naval Research Laboratory develops onion routing concept to protect government communications
- 2002: First public Tor prototype released, with .onion addressing system introduced
- 2004: Tor software becomes open source, enabling global volunteer relay network
- 2011: The New York Times launches first major news organization .onion service
- 2014: Facebook establishes official .onion address to bypass censorship
- 2020: Tor Project introduces next-generation .onion services with stronger encryption
This evolution demonstrates how privacy technology originally designed for specific government applications has become vital infrastructure for digital rights worldwide. The Tor Project's official documentation confirms these milestones through their historical development records.
Safety and Legal Considerations: What Users Should Know
Accessing the Onion Web carries specific considerations that responsible users should understand:
- Legal status varies: While accessing Tor isn't illegal in most Western democracies, some countries like China and Russia actively block and criminalize its use
- Security limitations: Tor protects network anonymity but doesn't make you immune to malware or phishing attacks
- Performance trade-offs: The multi-node routing creates slower connection speeds compared to standard browsing
- Content risks: Without proper precautions, users might accidentally access illegal or disturbing content
The Electronic Frontier Foundation (EFF) recommends using Tor Browser with JavaScript disabled for maximum security when exploring .onion sites. They emphasize that while the technology itself is neutral, users bear responsibility for their activities within the network.
Practical Guidance for Privacy-Conscious Users
You don't need to access the Onion Web to benefit from its privacy principles. Consider these practical applications:
- Use Tor Browser for sensitive research when public Wi-Fi networks are your only option
- Access news organizations' .onion services if you're in a region with heavy censorship
- Understand that privacy tools have legitimate uses beyond what's portrayed in media
- Support digital rights organizations working to preserve anonymity technologies
For most everyday privacy needs, standard HTTPS connections and reputable VPN services provide sufficient protection without the performance trade-offs of Tor. Reserve Onion Web access for situations where enhanced anonymity is genuinely necessary for your safety or professional obligations.











 浙公网安备
33010002000092号
浙公网安备
33010002000092号 浙B2-20120091-4
浙B2-20120091-4